How I got Interested
A few months ago I watched the film The Imitation Game. This peaked my interest and introduced a physical aspect to my concept of cryptography. To summarize very briefly the movie revolves around a device called the Enigma Machine, a machine used by the Nazi’s in World War II to encrypt and decrypt communications.
How the Enigma worked was that the sender would preconfigure a set to a predetermined inputs in the form physical settings that configured circuitry to generate a pseudorandom substitution of plaintext, that was then typed in, into ciphertext. The receiver would apply the same configuration to their machine and input the ciphertext, which would then output the plaintext.
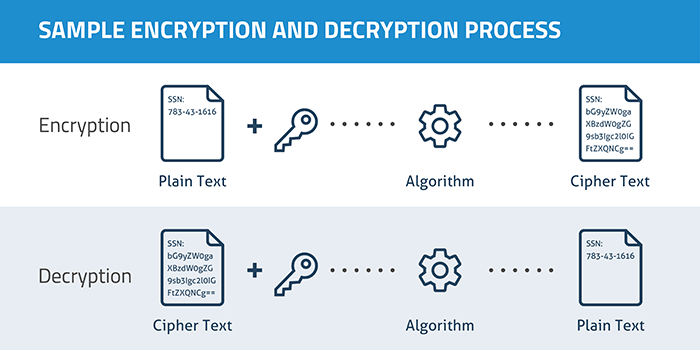
The conversion of plain text to ciphertext is called encryption, and the inverse decryption. In principle this seams quite simple and easy to crack, well in my mind it did. But I had a very shallow understanding of how complex transformations or the process of encrypting plain text could be.
The Enigma machine did not have a static transformation, much like what many people may understand when encoding letters or what you would find in an escape room. For example if you were to shift every alphabet one letter to the right, i.e. A->B, the encrypted text would look pretty weird at first but when you caught on it would be relatively easy to solve.
In the case of the Enigma, after each key was pressed the right hand rotor (one of the physical inputs to set transformations) was rotated a number of positions, changing the transformation of the next character. With a total sum of five rotors to chose from, three of which were placed in the machine, each with 26 positions, and a plugboard with 10 pairs of connected letters, thanks to cyclic permeation, had 158,962,555,217,826,360,000 different settings.
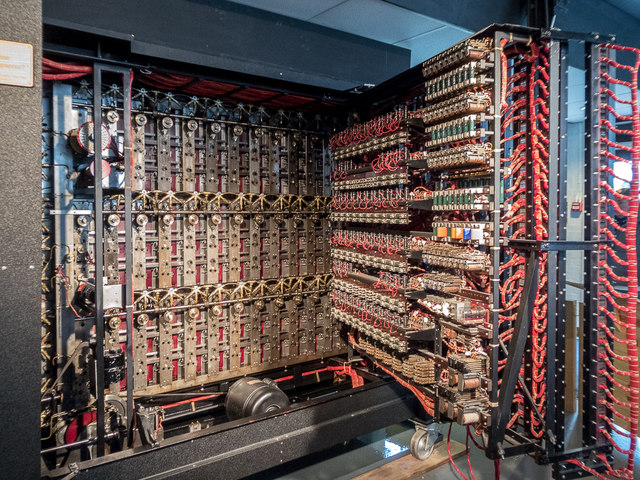
This was defiantly impressive for the time, however Alan Turing and various British cryptologists created an equally if not more impressive machine called the Bombe that was used to break Enigma’s encryption. To over simplify things, the Bombe would brute force the encryption and output Enigma settings that would decrypt ciphertext. They did all of this before computers were invented with macro scale parts. The bombe would often be referred to as the “First Computer”.
Two Fundamental Types of Cryptography
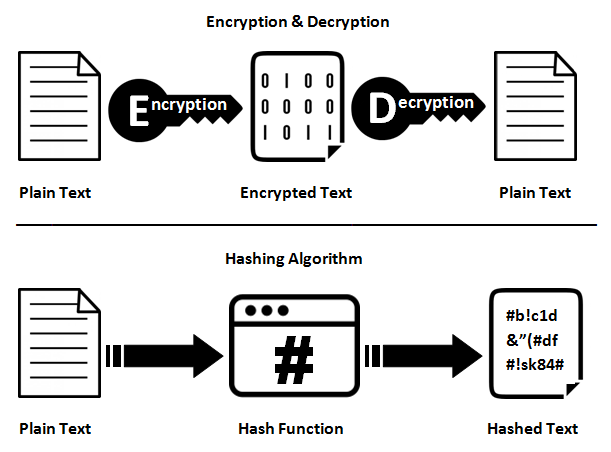
Fundamentals there exists two different types, or I should say uses for cryptography. Encryption, which is a two-way function and hashing a one way function.
Encryption
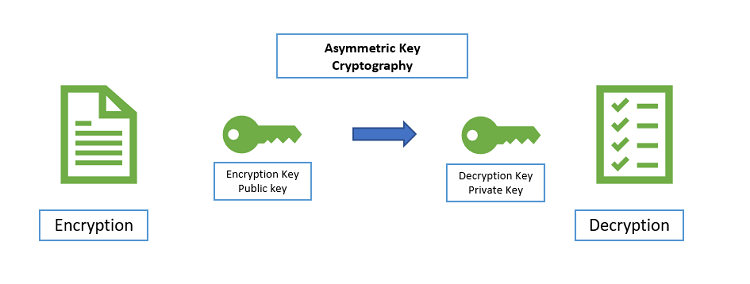
Encryption is used when the data or message being subjected to cryptographic functions needs to be reused by an end user. In the case of this cryptographic method, there is a key. The key is used to encrypt and decrypt the message such as in the case of the Enigma Machine, this would be a symmetrical encryption key, where both keys used to encrypt and decrypt are the same. In further advancements, such as RSA (Rivest-Shamir-Adleman) there are two asymmetrical keys. One private and one public, the public key can be used by anyone to encrypt messages, however the private key is needed to decode the encrypted message. This whole system relies on prime numbers and pretty advanced number theory. A whole post in its self could be dedicated on the topic of RSA, so I will leave it as that for now.
Hashing
Hashing on the other hand is a one way cryptographic function that is used to map data of any size to a standard output of a given size. This is very useful when verifying stuff where the end user does not actually need the data but needs to verify the data’s validity and integrity. One of the first advantages of this is that an input of any size, no matter how bug will only produce a hash of a given length, which would be a fraction of the original data’s size. Another benefit is due to how the transformations are done, hashing is many times faster than encryption.
For a hashing function or algorithm to be a SHA (secure hash algorithm) there are some criteria it must meet to provide the intended functionality of hashing. The two most important ones are; no two messages should have the same hash value and given a hashed message there can not exist a reverse function to reverse the hash and obtain the original message. One also unique property of hashing functions is the avalanche effect, where a small change in input causes a disproportionally large change in output. Given the unique nature of hashing some very interesting applications have been developed to utilized its unique property, one example is cryptocurrency, where hashing serves as a fundamental building block.
Whats to come.
Although this post was a deviation from my other posts (not that I have many). I plan to post a lot more randomly acquired knowledge to my blog. Many of which posts will encompass many of my fields of enjoyment such as engineering, tinkering, and the most recent cloud engineering. Also please visit my friend Lynn’s blog, she is a very talented cloud engineer with multiple interests similar to mine, and is also currently actively learning about blockchain technology.
Her blog an be found here https://www.lynnux.io/.




This Post Has 3 Comments