Terraform Tips & Tricks – Part 1 – Building A Constant Reference
One of the most common problems I see in large organizations when working with terraform is consistency. When we have a large amount of resources being managed…
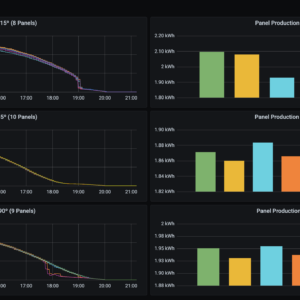
How to Monitor Your Enphase Home Solar System with Telegraf
How to collect metrics from an Enphase Envoy PV system, with telegraf and influxdb.
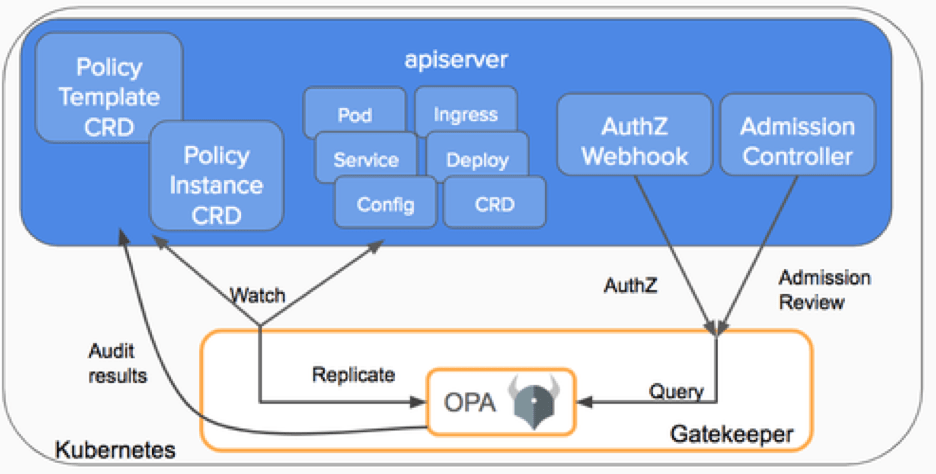
OPA Gatekeeper: Bringing Law and Order to Kubernetes
Introduction Open Policy Agent (OPA) is a policy based control agent that is able to be integrated on various platforms. For the sake of this document we…
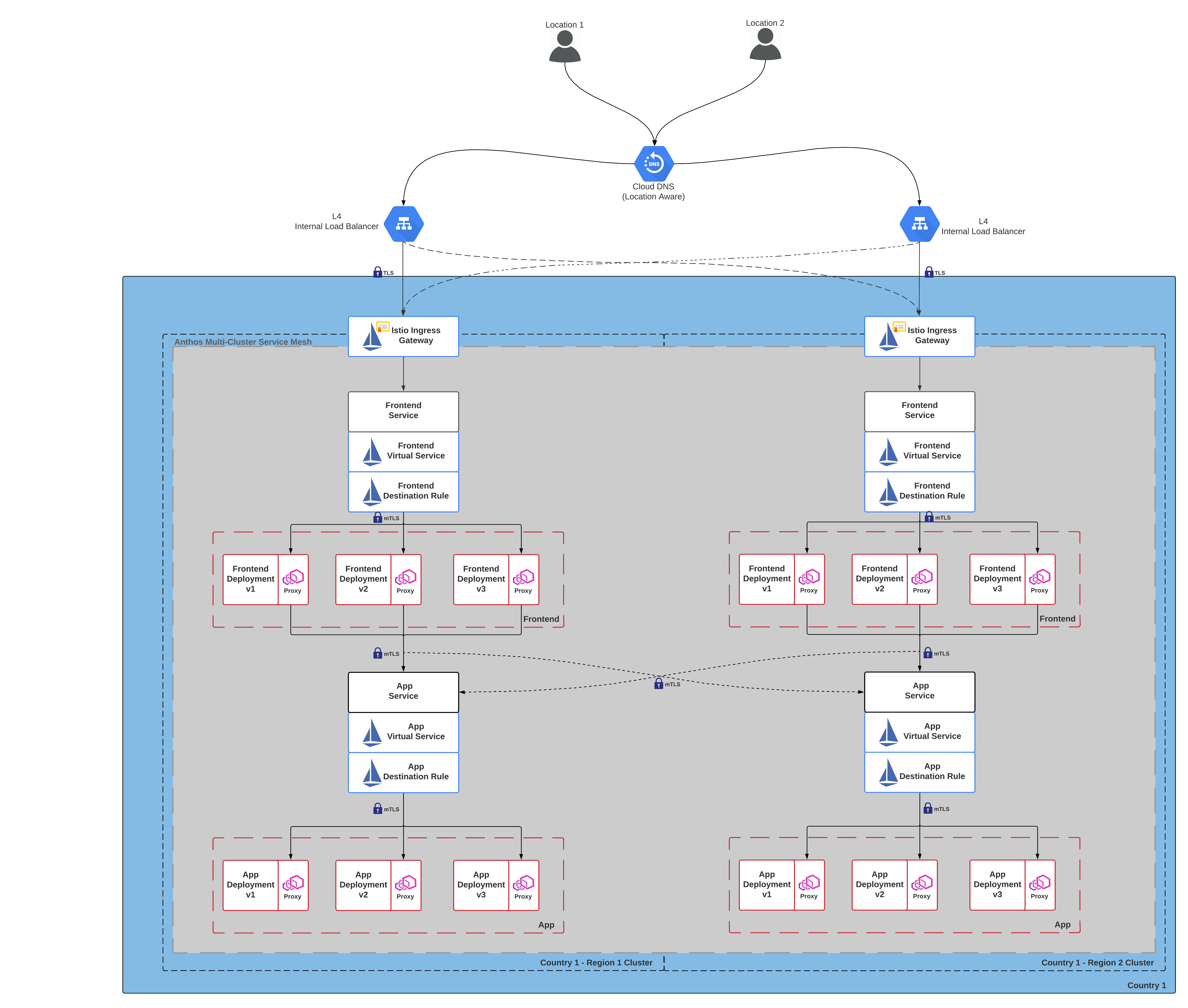
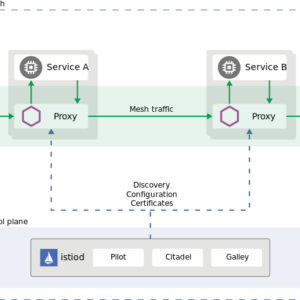
How to Setup Anthos on GKE Autopilot with Private Certificate Authority
What You Will Create The guide will set up the following: 2 Private GKE autopilot clusters with master global access ASM with multicluster mesh IstioIngress gateway to…
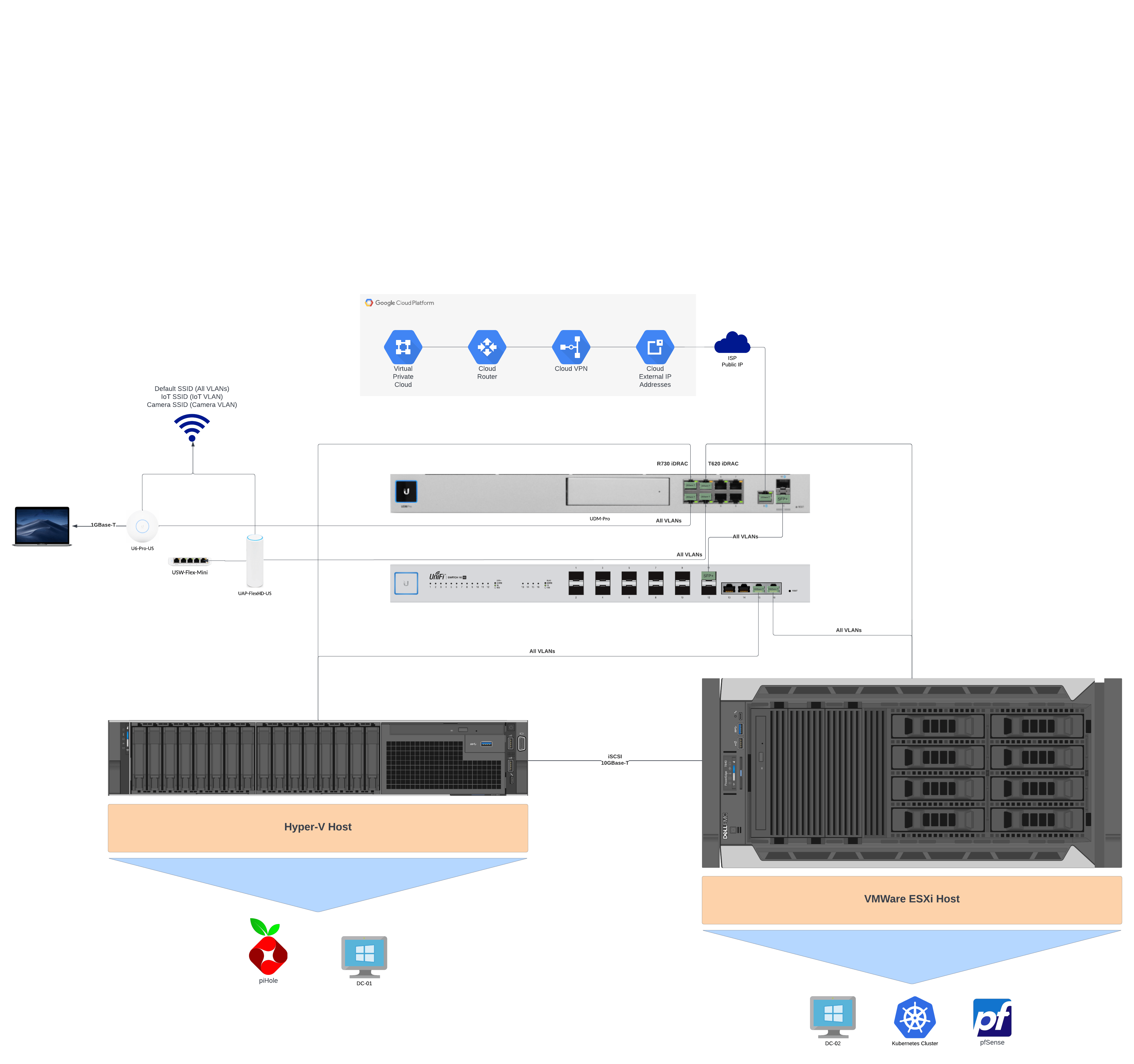
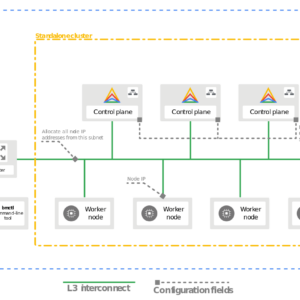
How to Setup a pfSense IPsec VPN Connection Behind a Router to Google Cloud
A tutorial on how to setup a virtual pfSense router behind a main router for VPN communications with Google Cloud Platform.
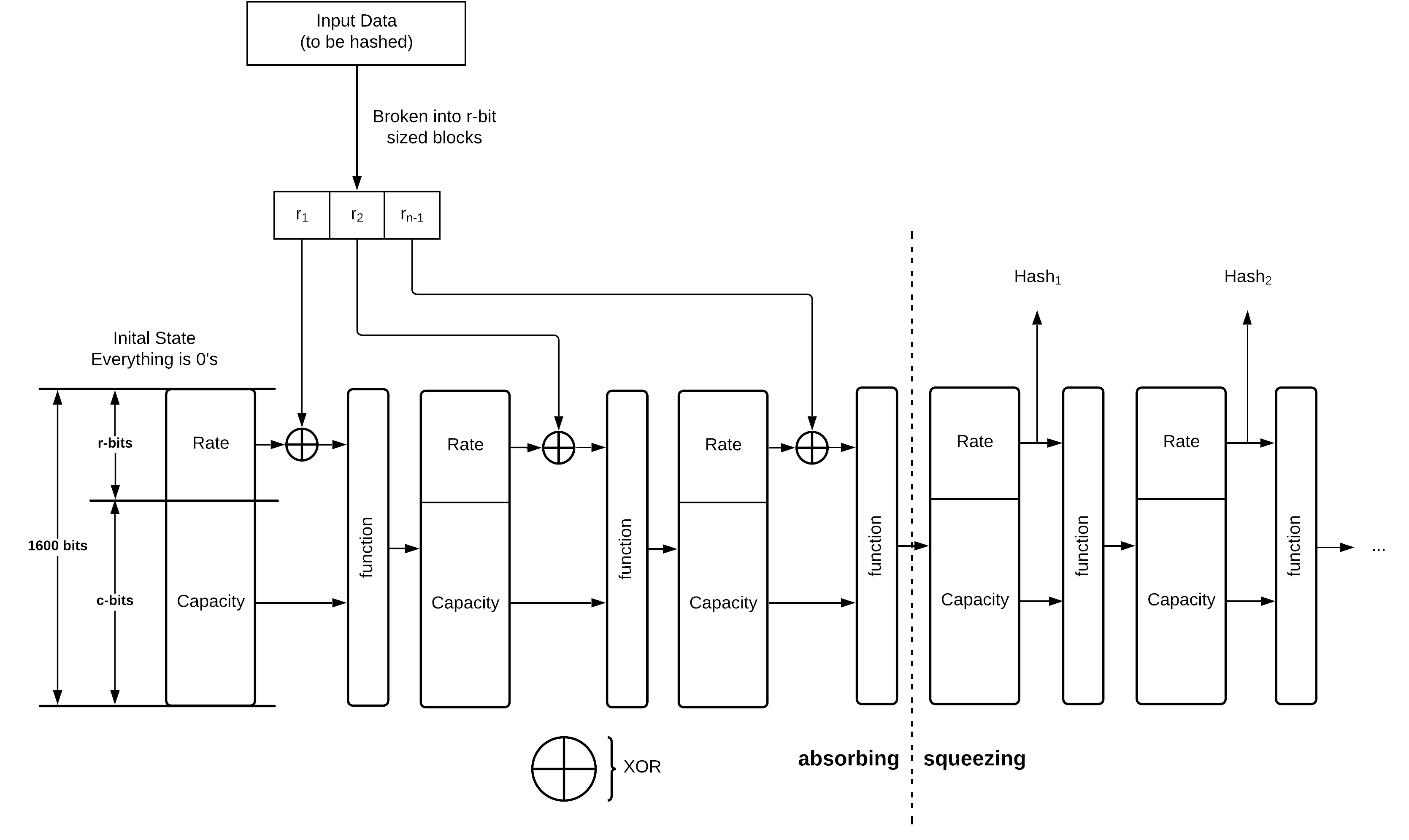
In-depth Visual Breakdown of the SHA-3 Cryptographic Hashing Algorithm
Background SHA-3 is short for Secure Hash Algorithm 3 This means that SHA-3 is a hash function and meets certain attack resistance criteria, if you don’t know…
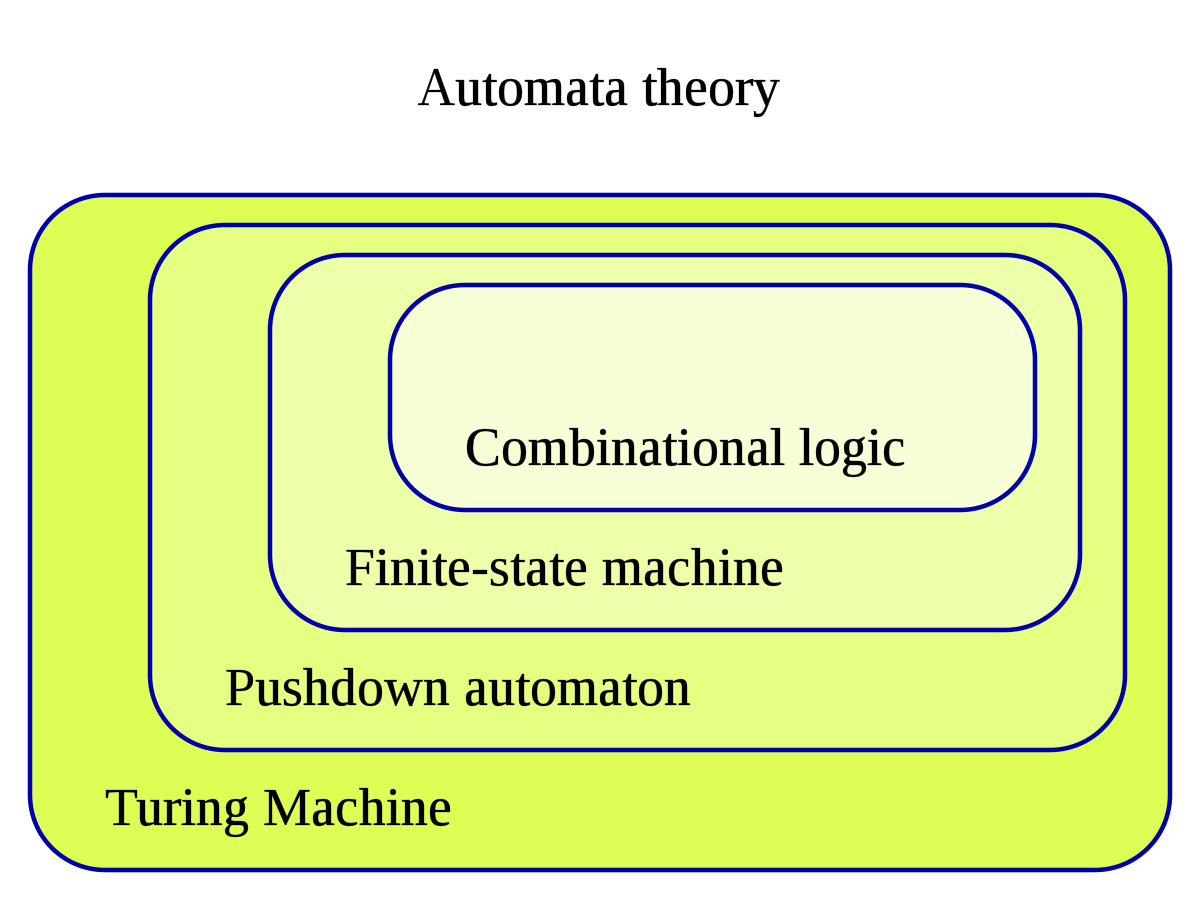
A Brief Explanation of Turing Completeness and Smart Contracts
Turing Completeness The concept of Turing completeness stems from Alan Turing’s definition of a Turing machine. I came across this concept after researching smart contracts. I saw…
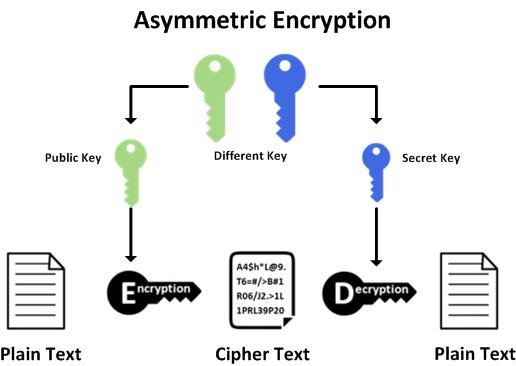
The Beautiful Mathematics Behind the RSA Cryptosystem
What is RSA? RSA or Rivest-Shamir-Adleman is a public-key cryptosystem that was first described in 1977 by Ron Rivest, Adi Shamir and Leonard Adleman. RSA is one…