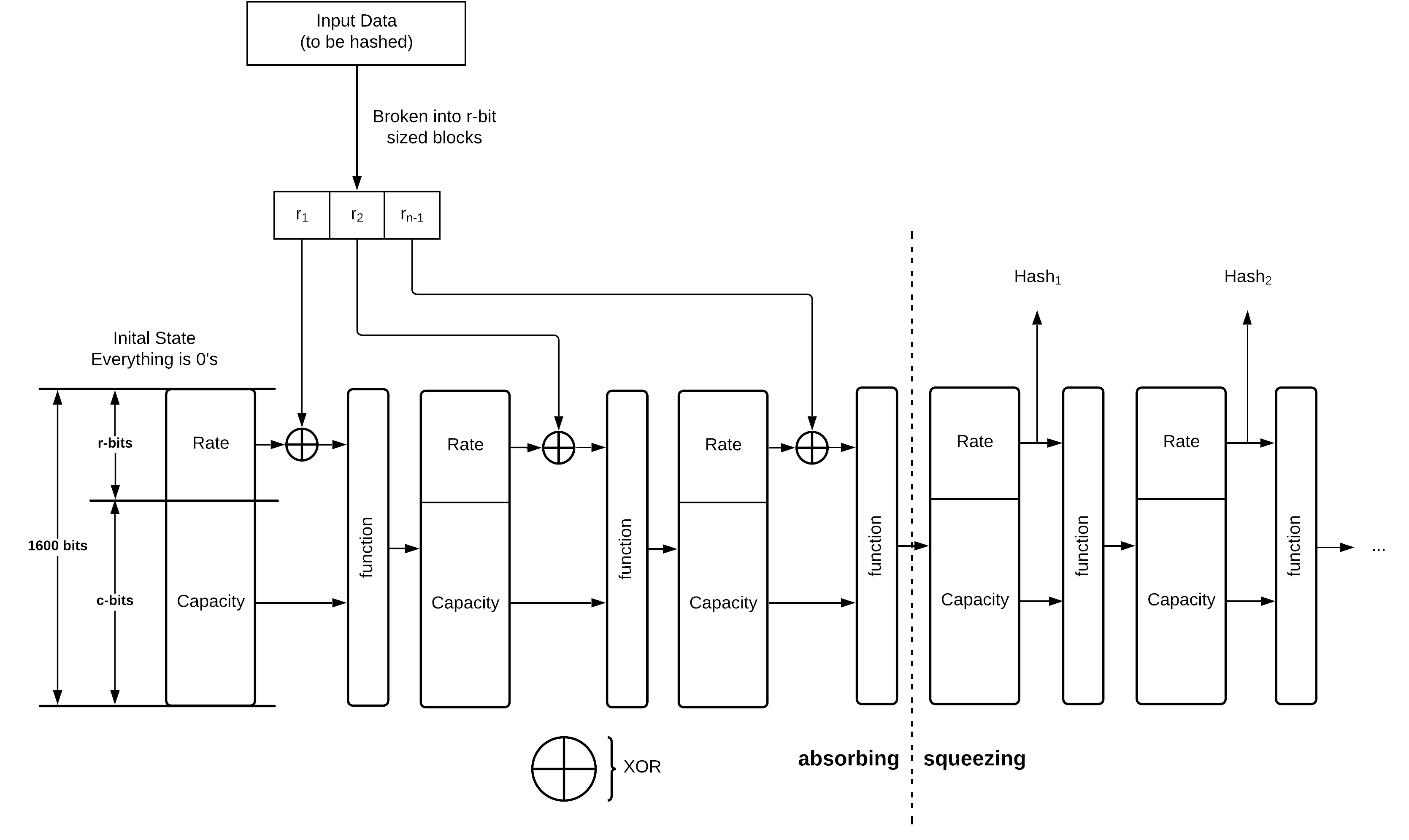
In-depth Visual Breakdown of the SHA-3 Cryptographic Hashing Algorithm
Background SHA-3 is short for Secure Hash Algorithm 3 This means that SHA-3 is a hash function and meets certain attack resistance criteria, if you don’t know…
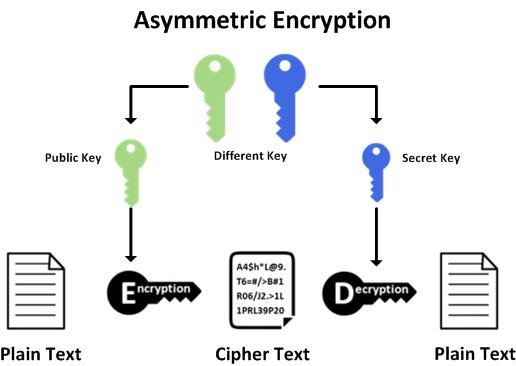
The Beautiful Mathematics Behind the RSA Cryptosystem
What is RSA? RSA or Rivest-Shamir-Adleman is a public-key cryptosystem that was first described in 1977 by Ron Rivest, Adi Shamir and Leonard Adleman. RSA is one…

Cryptography is the Mathematical Form of Art
How I got Interested A few months ago I watched the film The Imitation Game. This peaked my interest and introduced a physical aspect to my concept…